One of the hardest things about cybersecurity is communicating it to a non-technical audience and being understood. Cliff Stoll’s The Cuckoo’s Egg is a seminal cybersecurity book that achieves this beautifully. Published in 1989, it captivated audiences with a true story about a cyber intrusion involving multiple three-letter agencies and countries.
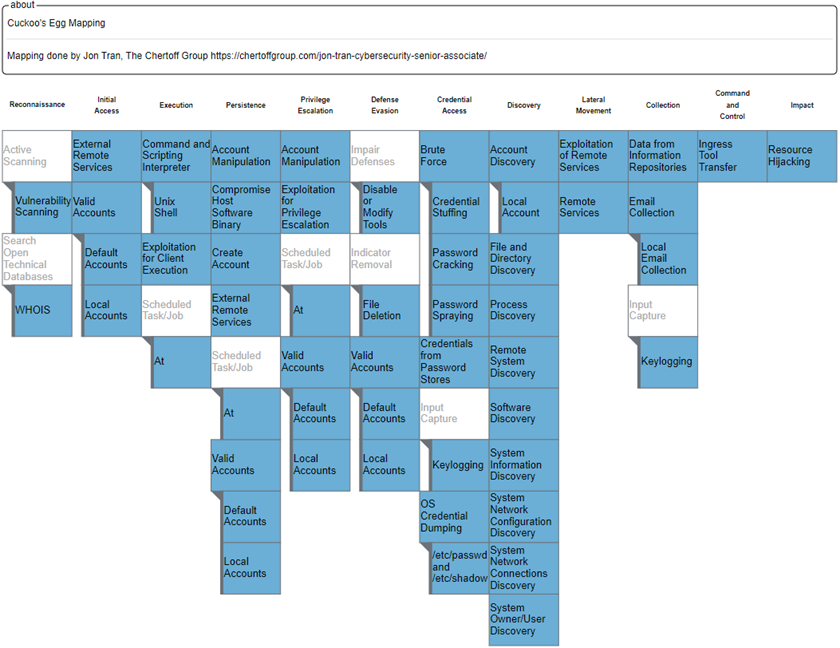
How does a book written in 1989 about an intrusion in 1986 hold up in today’s fast-paced cybersecurity threat landscape? Using the MITRE ATT&CK Framework, we can analyze the cyber intruder in The Cuckoo’s Egg. By applying the MITRE ATT&CK Framework, The Chertoff Group has mapped each step of the intrusion, offering a fresh perspective on this cybersecurity classic.
Using MITRE’s catalogued techniques, we can explain to a non-technical audience how these concepts apply today, demonstrating that foundational security principles from as far back as 1986 are still relevant. The intruder’s use of Default Accounts (T1078.001) could have been easily mitigated by implementing Password Policies (M1027), which would have disrupted most of the attack chain and prevented lateral movement. In addition we can compare the mitigations and data sources Cliff used to catch his hacker with those available today, highlighting additional mitigations, data sources, and new technologies such as EDR that weren’t accessible to him at the time
Upload this file to to see the mapping to Cliff Stoll’s a Cuckoo’s Egg against MITRE ATT&CK Framework. Find the Cuckoo’s Egg mapping file here and upload to MITRE ATT&CK Navigator.
How can The Chertoff Group help you tell your cybersecurity story?
Jon Tran is a Senior Associate at The Chertoff Group, where he uses his years in the Marine Corps as a Sysadmin, Information Assurance Professional, and Cyber Protection Team leader to ensure well rounded and understandable threat and risk assessments. Watch Jon’s presentation at MITRE ATT&CKcon.






